Elliptic Curves In-Depth (Part 2)
Last time around, we defined what elliptic curves are, and we devised a (suspiciously convoluted) way to add points on the curve together. And we hinted at how this operation was key for cryptographic applications.
However, the curves themselves — defined over the real numbers — are not the constructions we’re after.
Cryptography is a discipline of discrete precision. We want algorithms that yield consistent, reproducible results. In other words, we’re after determinism, which roughly speaking means that using the same inputs should yield the same outputs, no matter what.
Working with real numbers is quite cumbersome in this sense, because we normally use floating point arithmetic, and consequently, rounding errors are always present, making operations imprecise.
Due to rounding errors, the result of adding may not even land exactly on the curve (when working over the real numbers).
This calls for a different strategy.
That will be our starting point for today! We’ll kick things off with a minor detour, and then come right back to elliptic curves.
A Suitable Domain
As opposed to the real numbers, the integers are very precise to operate with. Since there are no decimals to worry about, rounding errors seem to be off the menu!
While this is true for addition, subtraction, and multiplication, it looks like division might be a bit of a problem: divided by clearly does not yield an integer, and we’re back in the realm of floating point arithmetic.
It’s also worth asking ourselves how large we can allow our integers to be. After all, we need to represent them somehow — and allowing them to grow too large is problematic when trying to store and handle them in a computer.
So yeah, integers — and more specifically, positive integers — , but we’re halfway there. We need a way to keep our values in check (bounded), while also figuring out how to handle division.
Modular Arithmetic
To remediate this, we’ll make use of a simple tool: the modulo operation, and modular arithmetic.
I’ve talked about this in previous articles, so I’ll assume familiarity with these concepts.
By using the modulo operation to bound results from our addition, subtraction, and multiplication operations, we essentially limit the possible integers we can work with to a finite set, such as this one:
We’re using the symbol here, because the resulting set will be a field (hence the ). A field is just a set where addition, subtraction, multiplication, and division are well-defined.
That’s one problem down (boundedness). Since our field is now a finite set, we just call it a finite field.
Division will require some more work — along with a clever observation.
A Different View
Take for example . Obviously the result is . How did we get there?
We can more rigorously describe the process as finding a solution to this equation:
And requiring to be a value between and (an element of ). This results in and .
It’s clear, however, that other solutions exist. For example, and . As you can probably tell by now, we can find infinitely many integer solutions to this equation.
In fact, the set of all possible values for forms an equivalence class.
Yeah ok... Why should we care? Turns out that by looking at it this way, there’s something we can do about division!
If we really think about it, the result of some division is nothing more than another number, which satisfies a particular property. For instance, the result of is , and for , we get . These results all share this property:
So, instead of thinking in terms of division, let’s think of it in terms of finding a reciprocal number. We ask ourselves:
![]()
![]() Given some number in our field, can we find another number (also in the field), so that when we multiply them together, the result is ?
Given some number in our field, can we find another number (also in the field), so that when we multiply them together, the result is ?![]()
![]()
In other words, we’re after a solution to this equation:
Which — you probably guessed it — can be translated into this form:
And we’re back in the scenario from before! If we happen to be able to find a valid value for , we say it’s the modular inverse of , and we write it as .

This form is known as Bézout’s identity, and we of course only care about integer solutions for and (it’s a linear Diophantine equation).
Importantly, a solution might not exist. Excluding zero, the condition for the modular inverse of an integer to exist is that it’s coprime with the field size , meaning that they share no factors — or that their greatest common divisor (GCD) is .
We can prove this very quickly. Suppose and share some factor , meaning that and . Then, we could factor out, and the above equation would become:
No matter what values of and we use, the left-hand side will never be , meaning that the equation would have no solution. Consequently, if a and share factor, then the modular inverse doesn’t exist.
There’s a very simple workaround for this: choosing a prime number for ! By definition, any prime number has only two factors: , and itself — meaning that, as long as the finite field has a prime size, then all of its elements (excluding zero) will have a modular inverse.

Well, in fact, by definition, the inverse of is .
Awesome stuff! This means that something akin to division is defined for every element in the set — it’s indeed a field.
Back to Elliptic Curves
Operations between elements of a finite field yield deterministic and well-defined results, which is exactly what we wanted!
Now all we need is to define our elliptic curves over these sets, instead of over the real numbers. There’s nothing too fancy going on here — we have already derived explicit formulas for point addition and doubling in our previous encounter. The only tweak we must do is to replace division with multiplication by modular inverses.
For example, point doubling is done by simply running these calculations below:
So yeah, nothing fancy — except that all those results are taken modulo . We also know that they are elements in our finite field — meaning that the resulting will have integer coordinates as well.
There’s a subtlety to be noted here. When we analyzed the case in the real numbers, we were guaranteed to find a third intersection point. It’s not immediately obvious that this translates to a finite field setting. Luckily for us, adding and doubling operations are also pretty well-behaved on finite fields!
Because of this, elliptic curves will not look like “curves” per se when defined over finite fields. Instead, they will look more like a set of points bounded to a square of side length , like this:
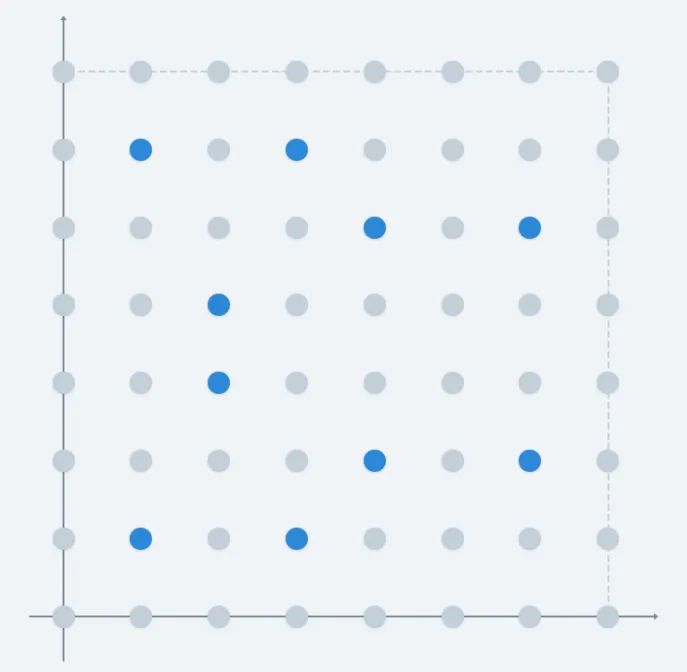
You can play around with different curves here.
And of course, we're not counting the point at infinity!
It’s not evident just by looking at this picture what the result of adding any two points on the curve is. Still, the chord and tangent rules are defined by the equations we already derived, regardless of the fact that we’re working with a different set. It’s just that visuals don’t help much now:
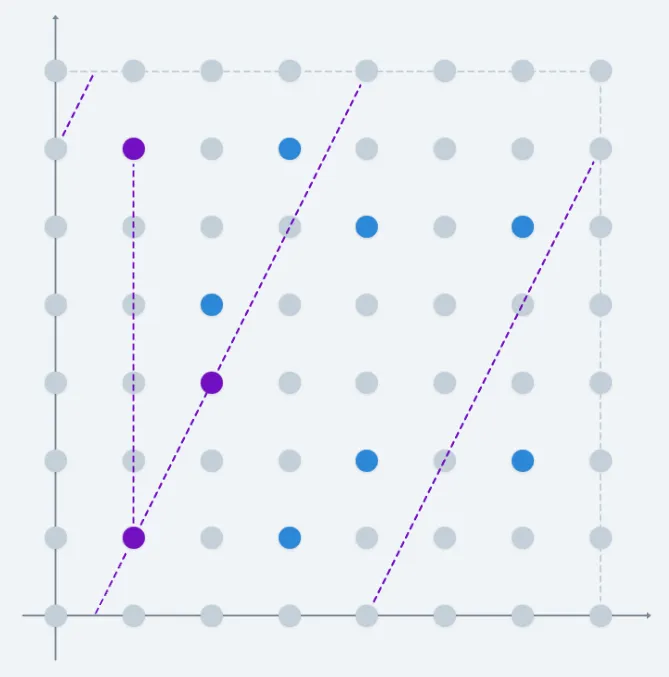
As you can see, the lines get cut when they reach the boundaries of our square domain — and this makes sense, because the lines are also defined modulo .
Everything is defined modulo now!
A more natural way to think about this, is by noting that the left and right borders are equivalent under modulo (), so if we could bend our square into three dimensions, we could paste those edges together, getting a 3D cylindric surface. Let’s explore this, just for fun.
The same can be done with the top and bottom edges. It takes a bit of imagination, but it’s as if our elliptic curve is really defined over a doughnut-shaped domain — a torus. In that space, the lines would effectively be continuous!
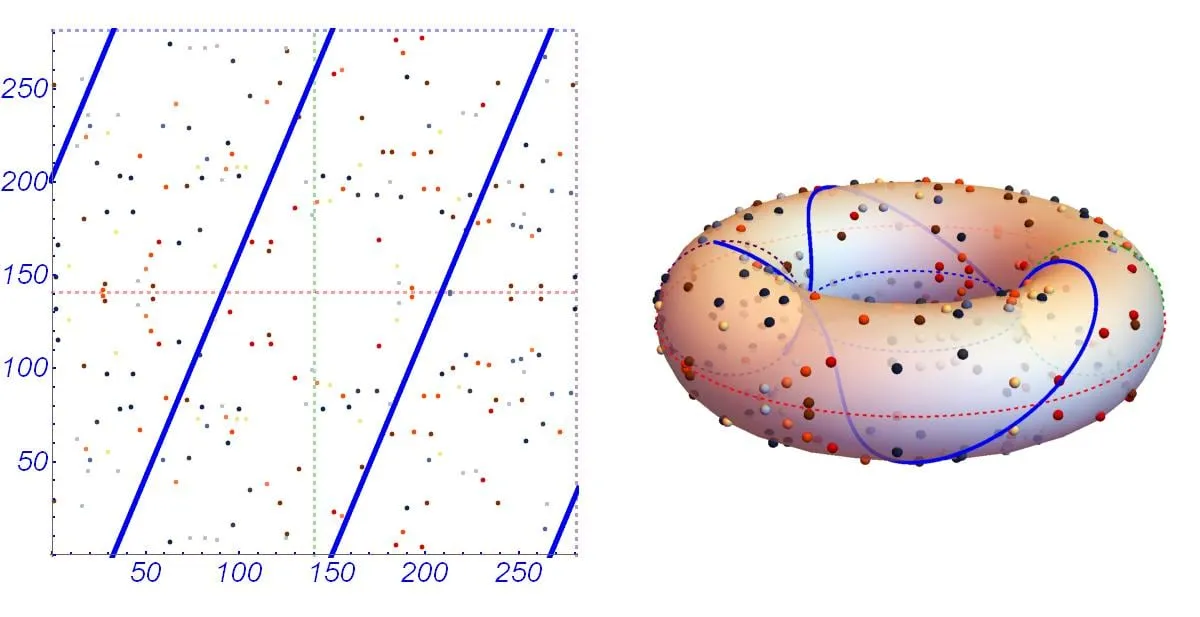
For those out there who have studied topology, this will be very reminiscent of quotient topologies!
We need not care for these transformations, but it’s always a good exercise to try and push our understanding a bit further, as it may help gain new insights.
Speaking of which — there’s a particularly pesky point we haven’t dealt with very gracefully so far: the point at infinity. It feels a bit forced — we can’t seem to place it anywhere. And after our little exercise with bending and doughnuts, let’s see if we can find a way to place it somewhere.
Projective Coordinates
Since our curve is defined over either or , it’s not crazy that we’ve pictured elliptic curves as points on a plane (or a deformed plane, in the cases we examined just moments ago).
This is called affine space (together with the point at infinity), sometimes denoted .
Here’s a rather unusual question: where can we place that plane? I mean, a plane is just a plane — an abstract canvas for us to represent things on. Does it even make sense to try to place it somewhere?
As a matter of fact, yes! And the first step to do so, is to move one dimension up.
In three dimensions, a plane is actually defined by a linear equation:
There are infinitely many different planes we could represent in three dimensions. Now “placing” a plane somewhere does make sense—all we need is to choose one of the infinitely many planes that are available for us in 3D space.
And we don’t need anything fancy, really. We can just choose the horizontal () plane that sits at . Imagine we draw our elliptic curve on this plane.
Here’s where it gets interesting: for each point on the curve, if we draw a line passing through the origin and , that line will intersect the plane at exactly one point: . So these lines are equivalent to the point themselves!
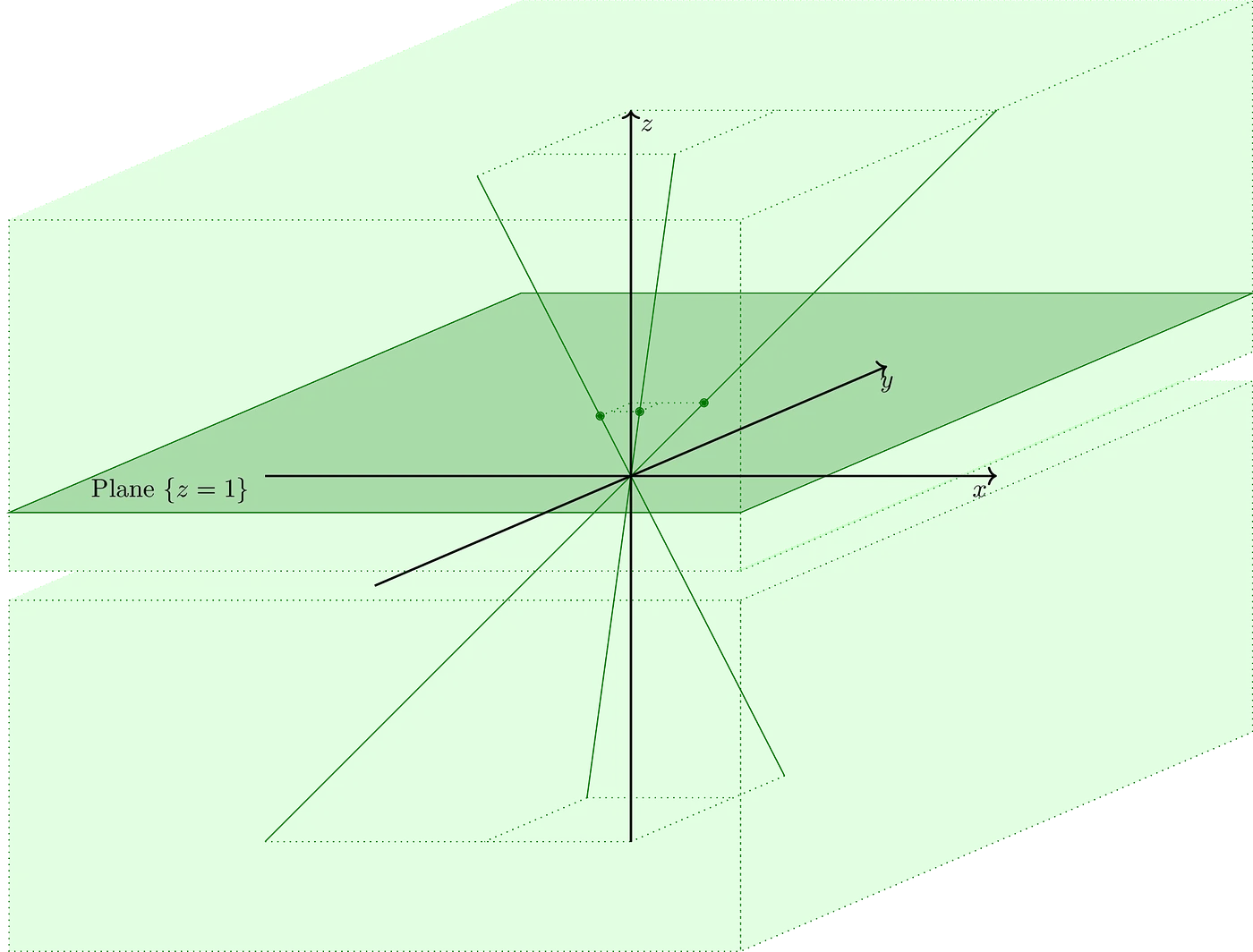
This is called projective space, and is denoted by . To make things a bit clearer, let’s denote points in this 3D space by .
Now, any point in any of these lines preserves the ratio . This is, if we examine the line defined by , then the point will lie on the same line, and so will , or generally speaking, any point of the form . This is usually represented via the notation to reflect this notion of ratios.
Because we chose , we can recover the original and values via:
And these expressions can be substituted into our elliptic curve equation, yielding this expression:
Which, after clearing the denominators, yields:
Let’s take a breather for a second. I must admit: this smells like an unnecessary complication.
But sometimes, these seemingly unnecessary complications can reveal new insights that may make our lives much easier.
Here’s a great video that perfectly illustrates this idea. It doesn’t have much to do with elliptic curves, but I think it’s simply amazing!
Upon closer inspection, something fantastic has happened indeed.
You see, every point on the curve that lives on the plane has the form . However, a “point on the curve” is really any point that satisfies the equation . There’s no real reason to restrict ourselves to a plane here.
Yet, we’re working with these projective coordinates — where each line starting at the origin is an equivalence class. And in this setting, there happens to be another point that satisfies the equation: the point . You can check this yourself — it just works!
This line is completely parallel to the plane — so it never intersects it. It satisfies the equation, yet it has no representative point in our affine space (the plane).
Sounds familiar?
Guess what — this is the point at infinity we’re looking for, but we can actually represent it now! Showing this fact takes a little effort, though. In the interest of not overcomplicating things, we’ll avoid going down that path.
Usefulness
Projective coordinates offer this new visibility over the point at infinity. Naturally, we may wonder if that’s all they are good for, or if it’s just an extremely contrived artifact to gain some additional understanding.
As it turns out, projective coordinates are quite useful! When we work out the formulas for point addition and multiplication, something interesting happens: we’re able to avoid some modular inverses!

Modular inverses are quite expensive to calculate. The standard algorithm to calculate them is the Extended Euclidean algorithm.
We’ll not be covering it here for the sake of brevity, but you can see how it works here.
What’s for sure is that it takes considerably more effort than simple multiplications. And so, using projective coordinates leads to faster elliptic curve operations!
In cryptography, where we need to perform thousands or millions of these operations, every little bit counts.
Summary
We’ve covered quite a bit of ground today! We moved from real numbers to finite fields, saw how our curves transform in this new setting, and even found a way to properly represent our point at infinity.
Of course, this is far from being the end of the story.
We have yet to talk about what makes elliptic curves useful in cryptography. But now that we’re working in this bounded setting, something remarkable happens: elliptic curves behave like groups. This is what gives them their cryptographic superpowers.
Next time, we’ll explore this group structure, see why it’s useful, and finally get to the heart of why elliptic curves are such a fundamental tool in modern cryptography.
Until then!

Did you find this content useful?
Support Frank Mangone by sending a coffee. All proceeds go directly to the author.
